A WPA network can be authenticated using different methods, which differ in ease of use, security, and efficiency. The WiFi authentication methods include the following:
Open Authentication
Open Authentication and WEP were the two methods for client authentication under the original 802.11 standard. Open Authentication authenticates the wireless hardware and the protocol to ensure that a client is an 802.11 device. When requesting to join wireless networks, a wireless client device must send an 802.11 authentication request and association request frames to the Access Point (AP).
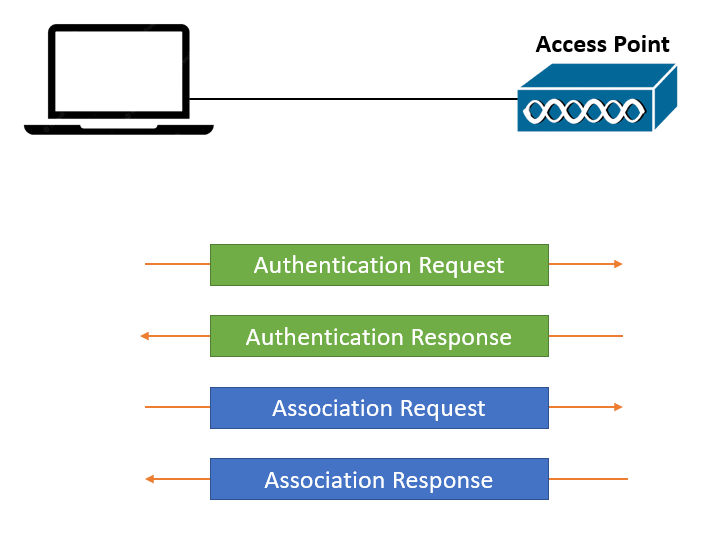
Open Authentication provides unrestricted access to a wireless network. All 802.11 clients may instantly authenticate and gain access to the network. WiFi authentication errors are rare. However, users must first open a web browser to view and accept the terms of use and provide their basic login information.
Network access is restricted until the credentials are entered. There is no authentication at the wireless level, but it is available at the upper layers. The traffic is not encrypted, and no additional credentials are needed.
Pre-Shared Key Authentication
The Wi-Fi Protected Access (WPA) versions support the Pre-Shared Key (Personal) and the 802.1x (Enterprise) client authentication modes. When using a Pre-Shared Key (PSK), a shared key string must be shared or configured on every client and AP network settings before the clients can access the wireless network.
The key string is never sent wirelessly. Both the client and the AP perform a four-way handshake process using the pre-shared key string to create and exchange encryption key material. Once that process is complete, the AP may authenticate the client’s identity, and they can secure the data frames transmitted over the air.
The pre-shared key is often kept private to prevent unauthorized access. However, since there is a single shared password, it can easily be leaked outside the organization, either intentionally or unintentionally.
A malicious attacker can listen and capture the four-way handshake between a client and an AP when using WPA-Personal and WPA2-Personal modes. The pre-shared key can be guessed via a dictionary attack. If successful, the attacker can join the network while pretending as a legitimate user or decrypt the wireless data.
WPA3-Personal manages to avoid those attacks by enhancing the key exchange between clients and APs using the Simultaneous Authentication of Equals (SAE) method, where the client and AP can start the authentication process equally and simultaneously. WPA3-Personal also supports forward secrecy, which prohibits attackers from using a key to decrypt data that has already been sent over the air.
802.1x Authentication
WPA-802.1x or WPA-Enterprise authentication utilizes multiple identities rather than a single password. A digital certificate or a set of credentials can serve as an identity. Every user must authenticate using Extensible Authentication Protocol (EAP) secure authentication methods and a unique identifier. Various identifiers can be specified, and MFA can be enabled for a more secure authentication process.
Until the client completes a successful authentication, an 802.1x-enabled port restricts access to the network. For a WiFi network, a wireless client can connect to an AP. However, if there is a WiFi authentication error or failure, it won’t be able to perform any other actions unless the authentication is successful.
With WPA2-Enterprise mode, advanced capabilities can be used, such as assigning endpoints to VLANs or assigning ACLs to particular sections after authentication.
Download our Free CCNA Study Guide PDF for complete notes on all the CCNA 200-301 exam topics in one book.
We recommend the Cisco CCNA Gold Bootcamp as your main CCNA training course. It’s the highest rated Cisco course online with an average rating of 4.8 from over 30,000 public reviews and is the gold standard in CCNA training:
