Packets should be marked by the endpoint or as close to the endpoint as possible to give an end-to-end and scalable QoS experience. QoS Trust Boundary provides the assurance in which device are we going to trust the marking of packets within the network. When an endpoint assigns a CoS or DSCP value to a frame or packet, the switch port to which it is connected can accept or reject the CoS or DSCP values. If the switch accepts the values, it signifies it trusts the endpoint and does not need to reclassify or remark the packets received from that endpoint. If the switch does not trust the endpoint, the QoS markings are rejected, and the received packets are reclassified and re-marked with the appropriate CoS or DSCP value.
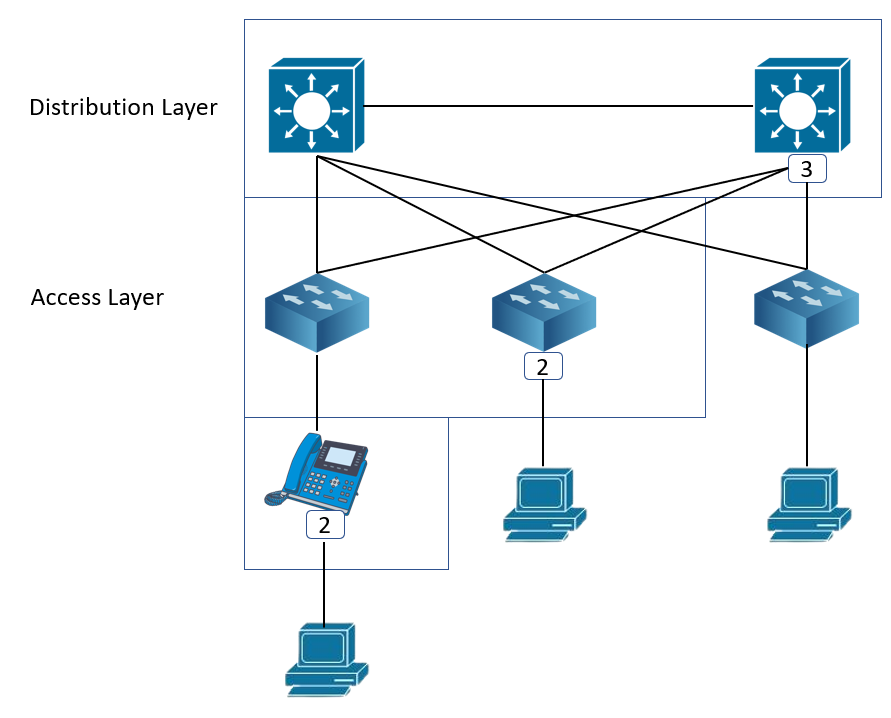
In the example above, Consider a campus network with IP telephony and host endpoints; by default, IP phones mark voice traffic with a CoS value of 5 and a DSCP value of 46 (EF), whereas incoming traffic from an endpoint like a PC is connected to the IP phone’s switch port is re-marked with a CoS value of 0 and a DSCP value of 0. The command mls qos trust cos is used to corresponding queue and mutate Cos to DSCP.
The default behavior for Cisco IP phones is not to trust the endpoint and zero out the CoS and DSCP values before delivering the frames to the switch, even if the IP precedence endpoint is providing incoming frames or tagged frames with a specific CoS or DSCP value. Because of the high-priority CoS and DSCP markings for voice traffic, when the Cisco IP phone sends voice and data traffic to the cisco switch, the cisco switches can designate speech traffic as a higher priority than data traffic.
Trust boundary categorization should be done as close to the endpoint as practicable for scalability. Trust boundary identifies on the figure above shows QoS trust boundaries at various points in a campus network, with 1 and 2 being the best options and 3 being acceptable only when the access switch is incapable of performing classification.
Wireless QoS
The QoS algorithms presented in this chapter can be used to configure a wireless network. For example, a wireless LAN controller (WLC) stands at the intersection of wireless and wired networks, making it an ideal site for a QoS trust boundary. Traffic entering and exiting the WLC can be categorized and labeled, allowing it to be handled appropriately over the air and on the wired network.
The four traffic types listed below can be used to construct wireless QoS on each wireless LAN (WLAN).
QoS Policy Categories and Markings
| QoS Category | Traffic Type | 802.1p Tag | DSCP Value |
| Platinum | Voice | 5 | 46 (EF) |
| Gold | Video | 4 | 34 (AF41) |
| Silver | Best effort (default | 0 | 0 |
| Bronze | Background | 1 | 10 (AF11) |
Download our Free CCNA Study Guide PDF for complete notes on all the CCNA 200-301 exam topics in one book.
We recommend the Cisco CCNA Gold Bootcamp as your main CCNA training course. It’s the highest rated Cisco course online with an average rating of 4.8 from over 30,000 public reviews and is the gold standard in CCNA training:
