Applying bulk changes to routes on a neighbor or peer-by-neighbor basis (or interface-by-interface basis for IGPs) does not easily allow for tuning of the network. By using BGP filtering with ACLs, network administrators can have precise control over the routing decisions.
BGP Filtering
BGP Filtering allows for customization of the network by selectively allowing or denying specific routes from certain neighbors or interfaces. Ultimately, this helps optimize network performance and security by filtering out unwanted traffic or unstable routes while ensuring optimal routing paths.
Access Control Lists
Access Control Lists (ACLs) were first designed to work as a basic firewall, BGP filtering packets coming into or going out of a network interface. Currently configured, ACLs offer packet categorization for multiple features, like filter lists and network identification inside routing protocols or quality of service (QoS).
ACLs provide a powerful tool for network administrators to control the flow of traffic within their network. By using ACLs, administrators can define rules that allow or deny specific types of packets based on various criteria, such as the source or destination IP address, protocol, or port number.
Access Control Entries
Access control entries (ACEs), entries in the ACL that specify the action to be executed (permit or deny), and the appropriate packet classification, contribute to ACLs. Until a pattern that corresponds is identified, packet classification starts at the top of prefixes lists (lowest sequence) and moves down (higher sequence) where the BGP filtering does its work. Once a match is discovered and prefixes, processing comes to an end, and the proper action—approval or denial—is done.
An implicit deny ACE, which rejects all packets that do not match the previously configured name in router BGP or the ACL, is included at the end of every ACL. This implicit deny ACE acts as a safety net, ensuring that any packet that does not have a specific match in the local router BGP or ACL will be denied access. with the help of BGP Filtering, it prevents unauthorized access and protects the network from potential security threats from any unwanted traffic.
BGP Filtering ACLs Classification
ACLs are classified into two categories:
- Standard ACLs define packets solely according to the source network. Standard ACLs are commonly used in situations where the network administrator wants to restrict access based on the source IP address. They are less flexible than extended ACLs, but they are easier to configure.
- Extended ACLs identify packets according to their source, destination, protocol, port, or a combination of other packet BGP attributes. Extended ACLs have the capability to apply stronger BGP filtering compared to standard ACLs. It considers additional packet BGP attributes such as destination IP address, protocol type, and port numbers. This makes it possible to filter, manage, and control network traffic.
Standard ACLs
The steps for defining a typical ACL are as follows:
Step 1. Define the ACL by using the command ip access-list standard {acl-number | acl-name} and placing the CLI in ACL configuration mode.
Step 2. Configure the specific ACE entry with the command [sequence] {permit | deny } source source-wildcard. In lieu of using source source-wildcard, the keyword any replaces 0.0.0.0 0.0.0.0, and the use of the host keyword refers to a /32 IP address so that the source-wildcard can be omitted.
BGP Filtering: Standard ACL-to-Network Entries
| ACE Entry | Networks |
| permit any | Permits all networks |
| permit 172.168.0.0 0.0.255.255 | Permits all networks in the 172.168.0.0 range |
| permit host 192.168.10.10 | Permits only the 192.168.10.10/32 network |
Extended ACLs
The steps for defining an extended ACL are as follows:
Step 1. Define the ACL by using the command ip access-list extended {acl-number | acl-name} and placing the CLI in ACL configuration mode.
Step 2. Configure the specific ACE entry with the command [sequence] {permit | deny} protocol source source-wildcard destination destination-wildcard. The behavior for selecting a network prefix with an extended ACL varies depending on whether the protocol is an IGP (EIGRP, OSPF, or IS-IS) or BGP.
IGP Network Selection
When ACLs are used for IGP network selection, the source fields of the ACL are used to identify the network, and the destination fields identify the smallest prefix length that is allowed in the network range. For routers using BGP filtering, the behavior is slightly different. During a BGP peering session, when ACLs are employed for BGP network selection, the source fields of the ACL identify the network range, and the destination fields specify the prefix length that is allowed for that network. Router BGP can achieve more granular control over which prefixes they advertise or which prefixes they receive.
Below are some example sample ACL entries from within the ACL configuration mode and specify the networks that would match the example extended ACL. Notice that the subtle difference in the destination wildcard for the 172.168.0.0 network affects the network ranges that are permitted in the first method second and third rows of the table.
BGP Filtering: Extended ACL for IGP Route Selection
| ACE Entry | Networks |
| permit ip any any | Permits all networks |
| permit ip host 172.168.0.0 host 255.240.0.0 | Permits all networks in the 172.168.0.0/12 range |
| permit ip host 172.168.0.0 host 255.255.0.0 | Permits all networks in the 172.168.0.0/16 range |
| permit host 192.168.10.10 | Permits only the 192.168.10.10/32 network |
BGP Network Selection
Extended ACLs react differently when matching routes in BGP filtering routes than when matching routes in IGP routes. When matching routes in BGP routes, extended ACLs have different reactions compared to when matching IGP routes. This is because the wildcard for the 172.168.0.0 network affects the permitted network ranges in the second and third rows inbound policy side of the routing table.
The source fields match against only prefixes in the network portion of the full route map, and the full route maps and map destination fields match against the network mask, as shown in the figure below. Until the introduction of the IP prefix list, extended ACLs were the only match criteria used with traffic in BGP filtering.
BGP Extended ACL Matches
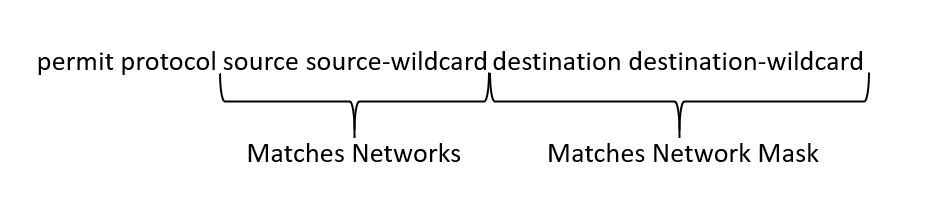
Extended ACL for BGP Route Selection
| Extended ACL | Matches These Networks |
| permit ip 10.0.0.0 0.0.0.0 255.255.0.0 0.0.0.0 | Permits only the 10.0.0.0/16 network |
| permit ip 10.0.0.0 0.0.255.0 255.255.255.0 0.0.0.0 | Permits any 10.0.x.0 network with a /24 prefix length |
| permit ip 172.16.0.0 0.0.255.255 255.255.255.0 0.0.0.255 | Permits any 172.16.x.x network with a /24 to /32 prefix length |
| permit ip 172.16.0.0 0.0.255.255 255.255.255.128 0.0.0.127 | Permits any 172.16.x.x network with a /25 to /32 prefix length |
Download our Free CCNA Study Guide PDF for complete notes on all the CCNA 200-301 exam topics in one book.
We recommend the Cisco CCNA Gold Bootcamp as your main CCNA training course. It’s the highest rated Cisco course online with an average rating of 4.8 from over 30,000 public reviews and is the gold standard in CCNA training:
