MAC Authentication Bypass (MAB) is not a secure authentication method, but it is an access control technique that allows port-based access control by using an endpoint’s MAC address. An interface with MAB authentication configured can be dynamically enabled or disabled based on the connected endpoint’s MAC address.
MAB is typically used as a fallback to 802.1x. For endpoints that don’t support IEEE 802.1X, such as printers and IP phones, MAB provides visibility and identity-based access control at the network edge. MAB can’t check anything besides the endpoint’s MAC address. Therefore, it does not offer secure authentication because MAC addresses are easy to spoof.
MAB Process Flow
The MAB authentication process consists of three steps, Initiation, MAC Authentication, and Authorization. The image below shows the MAB process flow:
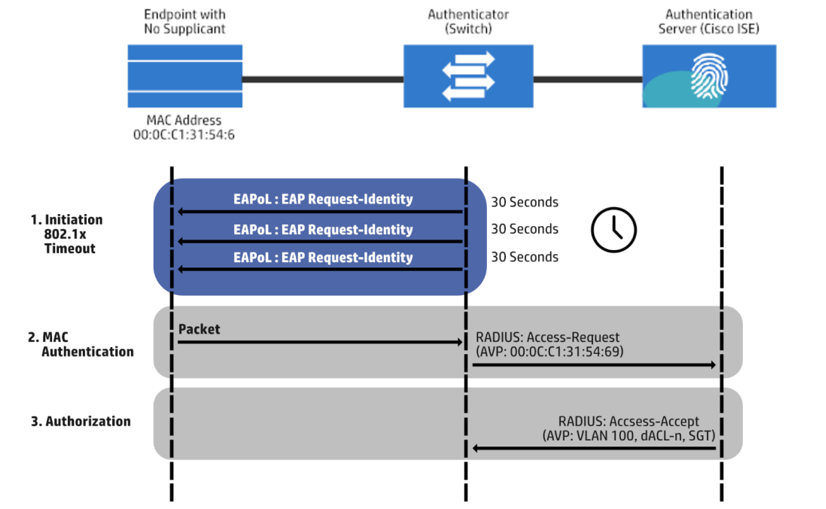
Initiation
Authentication is started by the switch submitting an EAPoL identity request. Then, every 30 seconds, by default, a message is sent to the endpoint. Three timeouts later, a total of 90 seconds by default, the switch indicates that the endpoint does not have a supplicant. Thus, it uses MAB to authenticate it.
MAC Authentication
In this step, the switch starts MAB by accepting a single packet from a single interface. It will use this information to determine the endpoint’s originating MAC address. Prior to it, packets that were sent back to MAB during the 802.1x timeout phase are instantly dropped and cannot be utilized to determine the MAC address. Once the switch identifies the source MAC address, it will discard the packet and will create a RADIUS access-request message with the MAC address of the endpoint as the identity. The RADIUS server will receive the RADIUS access-request message and proceed to perform MAC authentication.
Authorization
The RADIUS authentication server decides whether or not to give access to the device and what level of access it should provide. The RADIUS server provides the authenticator the RADIUS reply, access-accept, which allows the endpoint to have network access. It may also incorporate options for authorization, such as Downloadable ACLs (dACLs), Dynamic VLANs (dVLANs), and Security Group Tags (SGT), as a part of the authorization outcome from the authentication server.
MAB Authentication Advantages
Below are the benefits of enabling MAB authentication:
Visibility – MAB enables network visibility by allowing the IP address, MAC address, switch, and port of a device to be linked through the authentication procedure. Security audits, network forensics, network usage statistics, and troubleshooting all benefit from this insight. At the access edge, MAB operates as a Layer 2 controller, allowing you to regulate network access.
Identity-Based Services – MAB allows you to deliver dynamically configured services based on an endpoint’s MAC address. A device might, for example, be dynamically approved for a certain VLAN or given a unique access list that enables suitable access to that device. MAB is compatible with all dynamic authorization techniques that work with IEEE 802.1X authentication.
Fallback or Standalone Authentication – In a network with IEEE 802.1X-capable and non-capable devices, MAB can be used as a fallback or complementary authentication mechanism to IEEE 802.1X. If there is no IEEE 802.1X-capable device in the network, MAB can be used as a standalone authentication mechanism.
RADIUS Server Values – MAB also accepts dynamic RADIUS server values. You can utilize dynamic access lists and VLAN assignments in the same way that you can with 802.1X.
MAB Modes
MAB supports one endpoint per switchport by default. A security violation is flagged when it detects more than one source MAC address. The default mode can be changed to the following modes:
Single-Host Mode – the default mode where a single source MAC address can be authenticated. A security violation occurs when the switch finds another source MAC address after authentication. This is the default state.
Multi-Domain Authentication Host Mode – two source MAC addresses can be authenticated, one in the voice VLAN and one in the data VLAN. This mode is implemented when an IP phone and a PC are on the same switchport. Additional source MAC addresses result in a security violation.
Multi-Authentication Host Mode – several source MAC addresses can be authenticated. This mode is typically used when the switchport is linked to another switch because every source MAC address is authenticated independently.
Multi-Host Mode – allows multiple source MAC addresses. Just the first source MAC address is authenticated, and all other source MAC addresses are automatically permitted.
Download our Free CCNA Study Guide PDF for complete notes on all the CCNA 200-301 exam topics in one book.
We recommend the Cisco CCNA Gold Bootcamp as your main CCNA training course. It’s the highest rated Cisco course online with an average rating of 4.8 from over 30,000 public reviews and is the gold standard in CCNA training:
