802.1X authentication is a port-based network access control (PNAC) standard that opens ports for the network to gain access when an organization authenticates the user credentials and approves them for network access, enhancing network security.
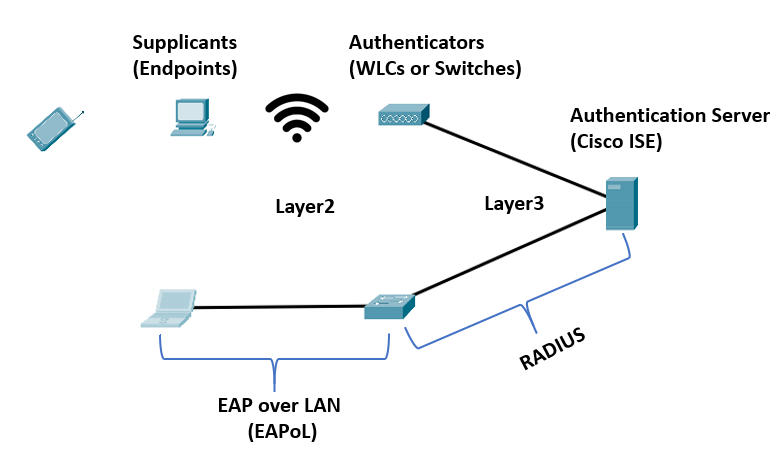
802.1x Components
The components of the 802.1x network authentication protocol are as follows:
- Extensible Authentication Protocol (EAP): RFC 4187 defines this message format and framework for encapsulated transport for authentication parameters.
- EAP Method/EAP Type: EAP supports a variety of authentication methods.
- EAP over LAN (EAPoL): IEEE 802.1x defines this Layer 2 encapsulation protocol for transporting EAP messages over IEEE 802 wired and wireless networks.
- RADIUS Protocol: The AAA protocol utilized by EAP.
802.1x Roles
The 802.1x network devices can employ the following roles:
- Supplicant: The endpoint software or client device is the supplicant. It communicates with the authenticator over EAPoL and gives identity credentials. Examples of supplicants are Windows, macOS, and Cisco AnyConnect. These supplicants support 802.1x authentication for both machines and users.
- Authenticator: The authenticator is a network access device (NAD), such as a switch, wireless access point, or wireless LAN controller (WLC). It restricts network access based on the user or endpoint’s authentication status. The authenticator also serves as a liaison, taking Layer 2 EAP-encapsulated packets from the supplicant and encapsulating them into RADIUS packets for delivery to the authentication server.
- Authentication server: The client’s authentication is handled by a RADIUS server. The authentication servers verify the endpoint’s identity and return an authorization result (accept or deny) to the authenticator.
802.1x Authentication Process
The EAP identity exchange and authentication happen between the authentication server and the supplicant. The authenticator doesn’t know the EAP methods used. It just takes the supplicant’s encapsulated EAPoL frame and encapsulates it within the RADIUS packet sent to the authentication server. The authentication server then instructs it to open the port. As a result, the authenticator is entirely unaware of the EAP authentication process.
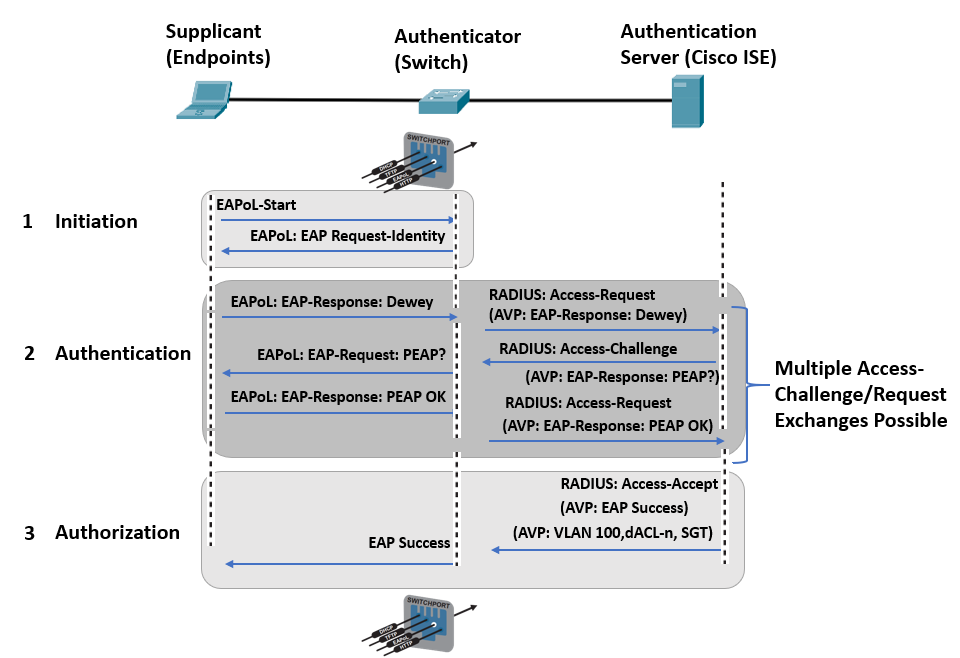
A successful 802.1x authentication process starts when the authenticator detects a new port that just came up. It initiates the authentication procedure by delivering periodic EAP requests. The supplicant can also begin the authentication process by delivering an EAPoL-start message to the authenticator.
The authenticator transmits the EAP messages between the authentication server and the supplicant. It copies the EAP message in the EAPoL frame to an AV-pair inside a RADIUS packet and vice versa until an EAP authentication method is chosen for the authentication to take place.
If authentication is successful, the authentication server responds to the client with an encapsulated EAP-success message within a RADIUS access-accept message and an authorization option. Once completed, the authenticator then opens the port.
Download our Free CCNA Study Guide PDF for complete notes on all the CCNA 200-301 exam topics in one book.
We recommend the Cisco CCNA Gold Bootcamp as your main CCNA training course. It’s the highest rated Cisco course online with an average rating of 4.8 from over 30,000 public reviews and is the gold standard in CCNA training:
