Virtual Network Function (VNF) is the virtual version of Network Function (NF), and it replaces dedicated hardware devices. Since VNF is virtual, it transforms the network hardware or Physical Network Functions (PNFs) of legacy network appliances and usually runs on a hypervisor as Virtual Machines (VMs).
VNFs deliver network functions and significantly speed up network services and network infrastructure deployment by substituting dedicated hardware appliances. Cisco has several VNFs, which include the following:
- Adaptive Security Virtual Appliance (ASAv)
- Advanced Malware Protection Virtual (AMPv)
- Cloud Services Platform 2100 (CSP 2100)
- Cloud Services Router 1000V (CSR 1000V)
- Email Security Virtual Appliance (ESAv)
- Integrated Services Virtual Router (ISRv)
- NextGen Firewall Virtual Appliance (NGFWv)
- Web Security Virtual Appliance (WSAv)
NFV Data Traffic Patterns
Understanding the purpose and the patterns of Virtual Network Functions (VNFs) is essential in determining which technology to utilize in switching traffic between VNFs and the outside world. Data traffic in Network Functions Virtualization (NFV) solutions follows two distinct patterns: East-West and North-South.
- East-West: The traffic enters the hosting server via a physical NIC (pNIC) and is forwarded to a VNF. Then, the traffic from the VNF could be sent to another service-chained VNF, which could also be service chained to other VNFs. The traffic will then be forwarded to the physical wire via the pNIC.
- North-South: The data traffic enters the hosting server via a pNIC and is forwarded to a VNF. Then, the data is sent from the VNF to the physical wire via the pNIC.
- Combination: Both patterns are used. The VNF utilizes the North-South data traffic pattern for user data and the East-West data traffic pattern to forward traffic to a VNF that is only used for statistics collection or for logs or storage.
Virtual Network Function Terminologies
Choosing the appropriate technologies will guarantee that the VNFs achieve the maximum throughput and performance. To do so, it is necessary to understand the following terms first:
- Input/Output (I/O): The data exchange between a computer system and the outside world. The data received by the computing system is known as the input, and the data sent from it is known as the output.
- I/O Devices: These are peripheral devices that include the mouse, keyboard, monitor, printer, Network Interface Card (NIC), etc.
- Interrupt Request (IRQ): A hardware signal sent by an I/O device to the CPU informing it that there is no data to transmit. When the CPU receives the IRQ, it saves its current state, temporarily suspends what it’s doing, and executes an interrupt handler routine associated with the device.
The interrupt handler identifies the causes of the interrupt, does the appropriate processing, restores the CPU state, and sends a return-from-interrupt instruction that allows the CPU to regain control and resume what it was doing before the interrupt. Every IRQ-generating I/O device has an interrupt handler that is a part of the I/O device’s driver.
- Device Driver: A computer program that commands I/O devices and connects the CPU to them. A Network Interface Card (NIC) is an example of an I/O device that requires a driver to operate and communicate with the CPU.
- Direct Memory Access (DMA): It is a memory access method that enables sending and receiving data on I/O devices. It can be direct to or from the main memory without passing via the CPU, speeding up computer operations in general.
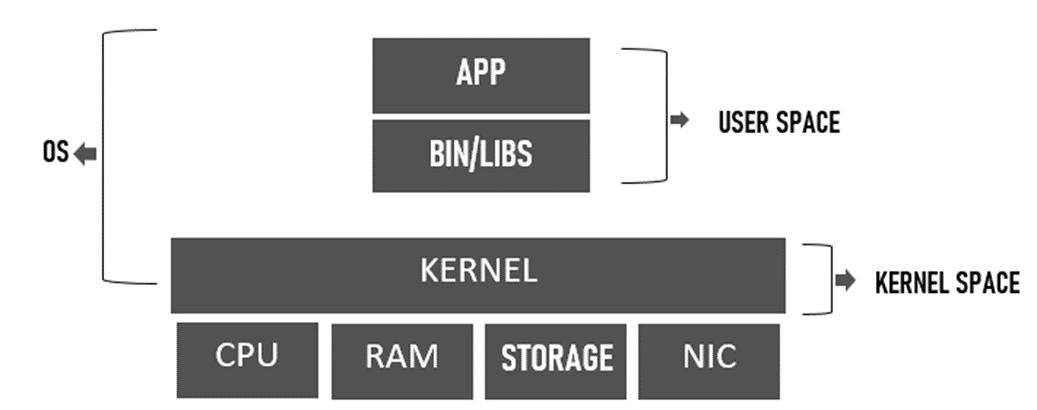
- Kernel and User Space: The kernel is a program that is considered the core or central component of an operating system (OS). It manages the hardware resources, including RAM and CPU. The kernel also provides system services to applications that require access to any hardware components, such as NICs and internal storage.
The kernel is operated in a protected section of the main memory called kernel space to avoid other processes from affecting it. Non-kernel processes run in a memory section known as user space, and it is the memory location where applications and their accompanying libraries are stored.
The figure below depicts the kernel, kernel space, and user space of an operating system (OS), as well as common I/O devices that are connected to the OS:
Download our Free CCNA Study Guide PDF for complete notes on all the CCNA 200-301 exam topics in one book.
We recommend the Cisco CCNA Gold Bootcamp as your main CCNA training course. It’s the highest rated Cisco course online with an average rating of 4.8 from over 30,000 public reviews and is the gold standard in CCNA training:
