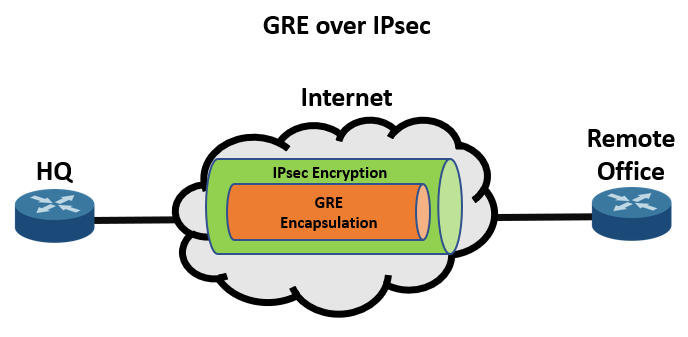
Generic Routing Encapsulation protocol was developed when security was not the primary concern. Therefore, GRE tunnels are often secured with IPSec encryption. IPSec is a collection of protocols that provide encryption for sensitive data and ensure end-to-end integrity of data.
IPsec before was used to support the encryption of unicast IP packets, making routing protocols like EIGRP experience issues because it uses a multicast address to establish neighbors.
Crypto Maps
There are two ways to implement encryption over a GRE tunnel: Crypto Maps and Tunnel IPsec Profiles. Encrypting traffic in a GRE tunnel using crypto maps is not recommended because of its limitations which IPsec profiles have addressed. These limitations include the following:
- MPLS is not natively supported
- Complex configuration
- Crypto ACL misconfiguration
- Crypto ACLs can take up lots of TCAM resources
Even though crypto maps are not recommended for tunnels, they are still used extensively and thus, should be understood. Here are the steps in configuring GRE over IPsec tunnels using crypto maps:
- Establish a crypto ACL to classify VPN traffic with the following commands. The access list will identify the traffic that IPsec will encrypt in the GRE tunnel.
ip access-list extended acl_name permit gre host {tunnel-source IP} host {tunnel-destination IP} - Configure an ISAKMP policy for IKE SA with the following command:
crypto isakmp policy priority
The priority value determines the IKE policy and assigns a priority, having 1 as the highest priority.
- The configurations that can be specified inside the ISAKMP policy include the following commands:
encryption {des | 3des | aes | aes 192 | aes 256} hash {sha | sha256 | sha384 | md5} authentication {rsa-sig | rsa-encr | pre-share} group {1 | 2 | 5 | 14 | 15 | 16 | 19 | 20 | 24}DES is the default encryption, but not recommended. 3DES is not recommended as well. The hash default is SHA, and MD5 is not recommended.
For authentication, digital certificates (rsa-sig), public keys (rsa-enrc), and PSK (pre-share) are allowed. The group assigns the DH group. 1 is the default configuration but is not recommended. It is recommended to use DH groups 14 and higher instead.
- Use the command below to configure PSK.
crypto isakmp key keystring address peer-address [mask]
The keystring value must be the same for both peers. You can use the 0.0.0.0 mask value to match any peer.
- A transform set is to be created using the command:
crypto ipsec transform-set transform-set-name transform1 [transform2 [transform3]]
- The IPsec tunnel mode can be set under the transport set configuration mode using the command:
mode [tunnel | transport]
- Create a crypto map with the command:
crypto map map-name seq-num [ipsec-isakmp]
- Specify the crypto ACL, IPsec peer, and transform sets to be negotiated using the following commands:
match address acl_name set peer {hostname | ip-address} set transform-set transform-set-name1 [transform-setname2...transform-set-name6]The acl_name must match the crypto ACL in step 1. The set peer command can be entered multiple times for multiple remote peers. The set transform-set lists the transform set/s to be negotiated, with the highest priority listed first.
- Apply the crypto map using the command to the outside interface:
crypto map map-name
Tunnel IPsec Profiles
Another way to implement encryption over a GRE tunnel is using Tunnel IPsec Profiles. Below are the steps in configuring a GRE over IPsec tunnel:
- Configure an ISAKMP policy for IKE SA and specify the encryption, hash, authentication, and DH group (steps 2-3 in the crypto map configuration). Configure the PSK as well (step 4).
- Create a transform set and specify the mode t be used (steps 5-6 in the crypto map configuration).
- Configure an IPsec profile with the command:
crypto ipsec profile ipsec-profile-name
- In the IPsec profile configuration mode, specify the transform sets to be negotiated, with the highest priority first, using the command:
set transform-set transform-set-name [transform-set-name2...transform-set-name6]
- Apply the IPsec profile to the tunnel interface using the following command:
tunnel protection ipsec profile profile-name
Verifying GRE over IPsec Configuration
There are several ways to verify if the GRE over IPsec has been established between the peers, which include:
- Using the ‘show interface tunnel value’ command, you can check if it’s a GRE tunnel.
R1# show interface tunnel300 | include Tunnel protocol Tunnel protocol/transport GRE/IP
- See the encrypted tunnel in the ‘show ip ospf’ neighbor’ command.
R1# show ip ospf neighbor Neighbor ID Pri State Dead Time Address Interface 2.2.2.2 0 FULL/ - 00:00:38 192.168.100.2 Tunnel100
- Check if the IPsec peer is learned over the tunnel using ‘show ip route {ospf | eigrp}’ command.
R1# show ip route ospf ! Output omitted for brevity Gateway of last resort is 100.64.1.2 to network 0.0.0.0 10.0.0.0/8 is variably subnetted, 3 subnets, 2 masks O IA 10.2.2.0/24 [110/26] via 192.168.100.2, 00:03:30, Tunnel300
- Verify the ISAKMP SA status with ‘show crypto isakmp sa’ command.
R1# show crypto isakmp sa IPv4 Crypto ISAKMP SA dst src state conn-id status 100.64.1.1 100.64.2.2 QM_IDLE 1008 ACTIVE
- Check the information of the IPsec SA with ‘show crypto ipsec sa’.
R1# show crypto ipsec sa ! Output omitted for brevity ! pkts encaps shows the number of outgoing packets that have been encapsulated ! pkts encrypt shows the number of outgoing packets that have been decrypted ! pkts decaps shows the number of incoming packets that have been decapsulated ! pkts decrypt shows the number of incoming packets that have been decrypted
Download our Free CCNA Study Guide PDF for complete notes on all the CCNA 200-301 exam topics in one book.
We recommend the Cisco CCNA Gold Bootcamp as your main CCNA training course. It’s the highest rated Cisco course online with an average rating of 4.8 from over 30,000 public reviews and is the gold standard in CCNA training:
