The Zone-Based Firewall is the most advanced and the latest integrated stateful firewall technology that is available on Cisco IOS routers. The traditional Cisco IOS stateful firewall, Context-Based Access Control (CBAC), is an interface-based configuration model wherein the interface is individually configured with a stateful firewall inspection policy. Traffic that passes through the interface receives the same policy and it also works alongside ACL.
Using CBAC produces multiple problems such as manual configuration on every associated interface which is time-consuming and prone to errors. Moreover, CBAC limits the granularity of firewall policy applications, especially firewall policies that are required to be applied between multiple interfaces. Zone-based firewalls overcome these limitations.
Zone-Based Firewall Configuration Model
The zone-based firewall utilizes a zone configuration model. Instead of assigning access lists, different zones are created and assigned to interfaces. The security policies are assigned to traffic between the zones. The zone-based firewall can also use CBAC commands concurrently on a router, but not concurrently on the router interfaces.
A router interface is assigned to only one security zone, which can have one-to-one or many-to-one relationships. Interfaces that belong to the same zone can communicate with each other freely and the interfaces which are in different security zones cannot communicate with each other by default.
A zone provides security by establishing security borders on the network. It defines the acceptable traffic that is allowed to cross between zones through the policy restrictions. Zone-based firewalls use a new configuration policy language called Cisco Activity Language (CPL).
Zone-Based Firewall Architecture
In the example topology below, there’s a WAN connectivity to the ISP, a LAN connection, and the DMZ. If we use access lists to set our security policies, then we have to individually specify the inbound and outbound access lists on the interfaces. It is tedious and time-consuming.
Using a zone-based firewall allows us to apply the said security policies to the security zones instead of the interfaces. Then, the interfaces are set as members of the different zones. In our example here, we have the following security zones:
- Outside Security Zone – interfaces towards a public network.
- Inside Security Zone – interfaces towards a private network.
- DMZ Security Zone – interfaces towards the DMZ.
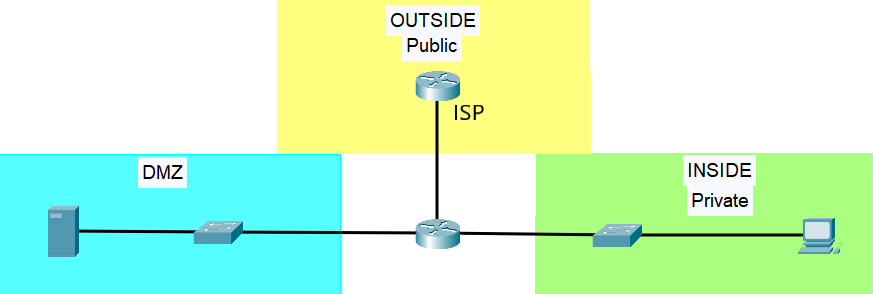
The outside security zone includes the interfaces for public traffic, such as connections to the ISP. The Inside security zone includes interfaces with traffic going to the private zone or to a LAN, and the DMZ zone includes interfaces with traffic going towards a neutral zone, the DMZ.
Zone pairs are needed to be configured in order to create a security policy for the traffic between security zones. Once the zone pair is configured, a security policy is then applied to the zone pair in order to specify which traffic is allowed from one zone to the other zone.
The Self Zone and the Default Zone
The zone-based firewall also has two system-built zones, which are the self zone and the default zone. Both zones are system-level zones and each zone includes different interfaces.
The self zone includes all of the IP addresses of the routers. The traffic going to and coming from the self zone is allowed to support management plane functions, such as SSH and SNMP, by default. It also supports control plane functions. An interzone communication must be defined after a security policy is applied to the self zone and to another security zone.
The default zone includes any interface that is not a security zone member. The traffic is dropped when an interface that doesn’t belong to a security zone sends traffic to an interface in a security zone. However, by enabling the default zone on the interface, a security policy can be configured. Thus, allowing a policy map to be created between two security zones and permitting traffic flows.
Download our Free CCNA Study Guide PDF for complete notes on all the CCNA 200-301 exam topics in one book.
We recommend the Cisco CCNA Gold Bootcamp as your main CCNA training course. It’s the highest rated Cisco course online with an average rating of 4.8 from over 30,000 public reviews and is the gold standard in CCNA training:
